IdM Best Practices...
Keys to a Successful IdM Deployment:
- Have an Airtight Deployment Strategy
- Accurate Data Discovery
- Combine with Process Engineering Effort
- Thorough Statement of Work
- Detailed Acceptance Criteria
|
|
- Customer's Deployment of an IdM Administrator
- Must be a Qualified Person
- Must Have Visibility across the Organization
- Must Know and Work with Other Application Administrators
|

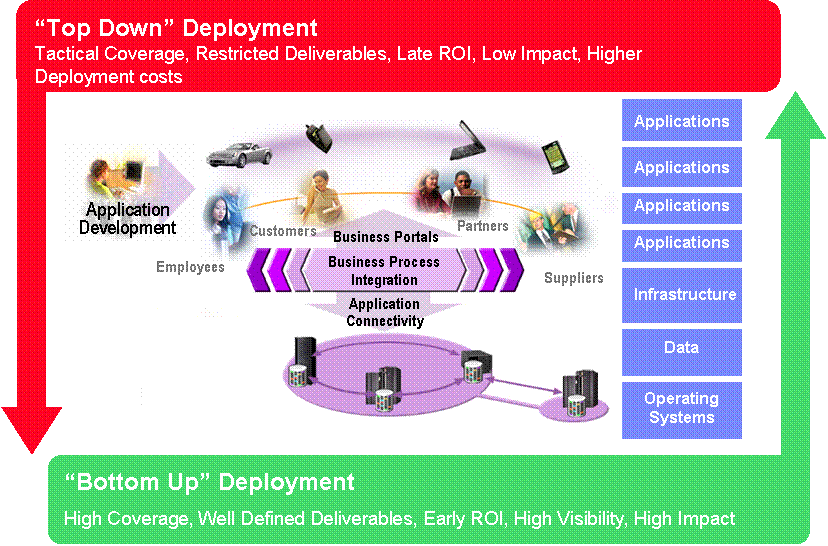
Deployment Approach Alternatives:
When planning for an Identity Management (IdM) deployment, there are two
opposite approaches that can be taken. One of these is the "top down"
methodology. The other is the "bottom up" methodology.

Which Approach to Use?
While either approach is valid, there are some basic guidelines that should be
taken into account when attempting to determine which methodology to use:
|
Option 1 – Bottom Up
For:
- User and business awareness of product and benefits are
visible from and early stage.
- Many manual processes can be replaced by automation.
- Password management can be implemented for a large number of
users.
- No development of agents required in phase 1.
- Broadens skills and understanding within your organization
at the first phase.
- Eases IdM gently into the business.
Against:
- Organizational structure may have to be altered at a later phase.
- Medium to high impact on system owners etc, co-operation required.
- Driven by Infrastructure, not Business.
|
|
Option2 – Top Down
For:
- Focused use of resources from the individual target.
- First implementation will be showcase of what can be done.
- Deep coverage of an application once IdM implementation has finished.
- Low impact on operation and maintenance resources.
Against:
- Limited coverage in the first phases, minimal % of user accounts managed.
- Potentially custom agents will have to be developed at an early stage.
- Minimal benefit to support and overall business.
- Higher implementation cost.
|

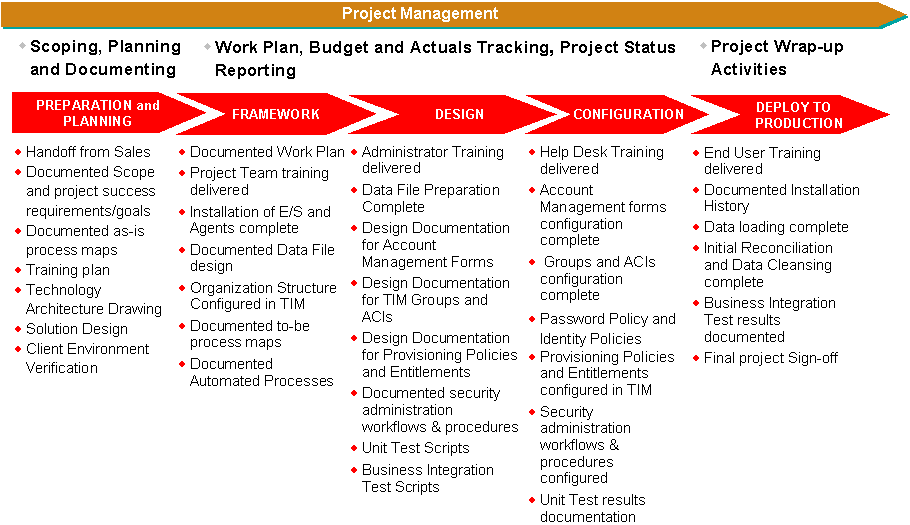
Project Management Considerations:
NetworkingPS will help you determine the best approach for implementing Identity
Management into your infrastructure. We can also provide you with overall project management during your
IdM
implementation, or assist you with any of the individual phases typical of such an implementation. Whether you are working with IBM Security Identity Manager (ISIM - formerly IBM Tivoli Identity Manager), Oracle Identity Manager (OIM), CA Identity Manager (formerly CA IdentityMinder), or Ping Identity Manager, NetworkingPS has the resources and skills to support you.
| 