Secure Remote Administration - Stand Alone Approach...
The Tracker
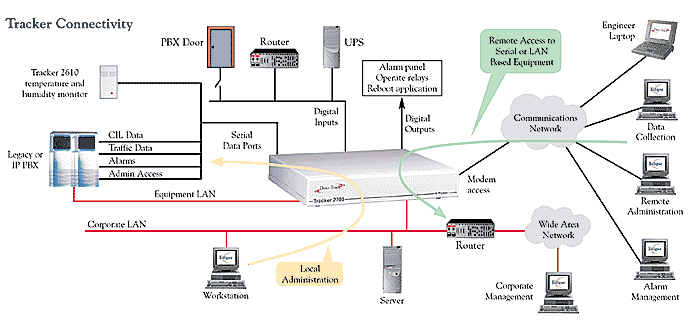
2750 by Data Track Technologies, Plc. incorporates a design that is unique to
the industry to provide greater flexibility in terms of the unit’s inputs
and outputs. I/O is provided by interchangeable plug-in cards that can
be slotted into a motherboard. It has an RJ45 serial console port that is
fitted on all units. There are 9 expansion slots available for the addition of
a variety of I/O cards containing serial ports, modems, Ethernet ports, or
digital I/O ports. Memory is provided using compact flash cards. This enables
much larger memory options (currently up to 3 Gbytes) ... more than any other
manufacturer.

|
 |
| |
|
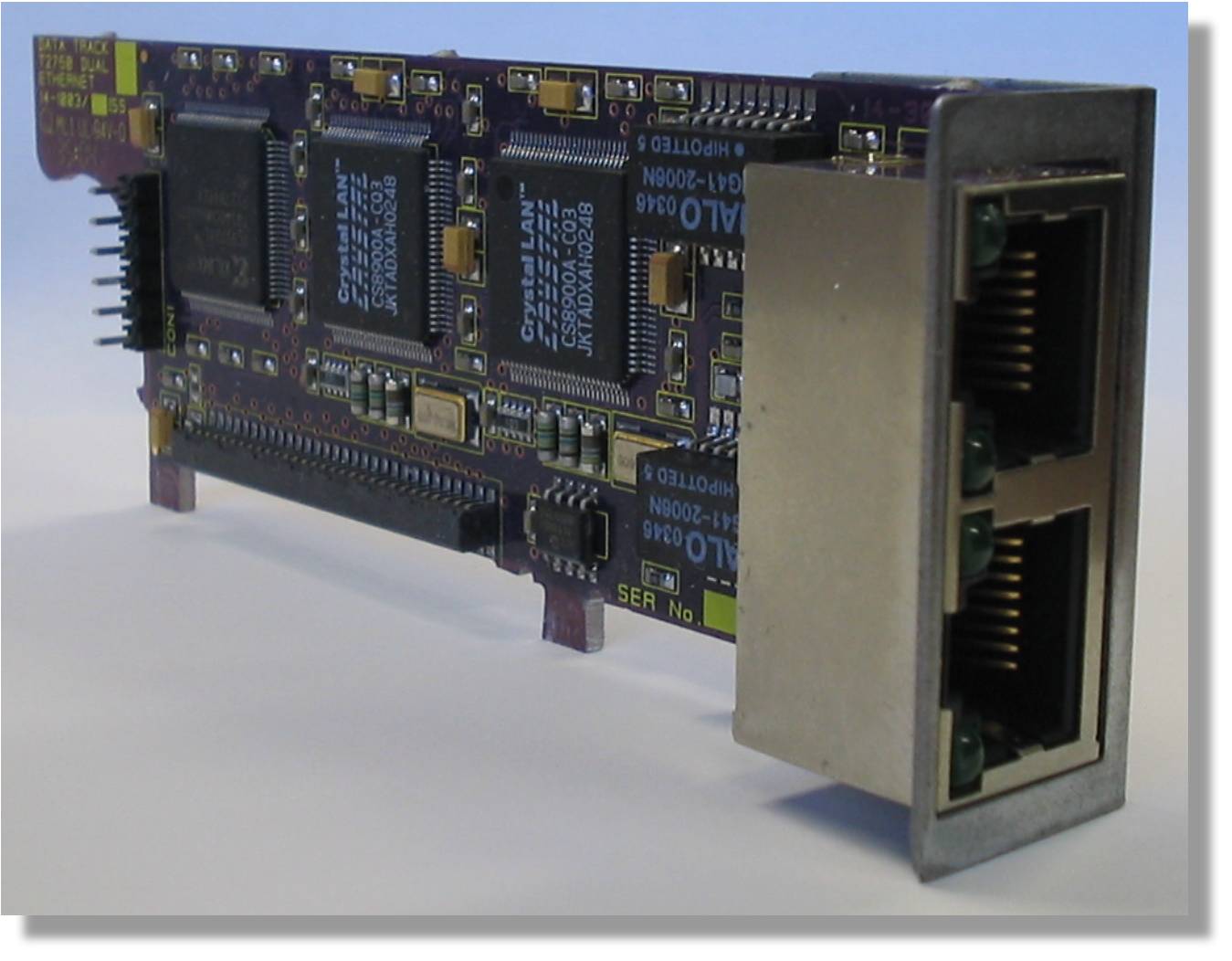
Single and dual 10 /100MB Ethernet card
|
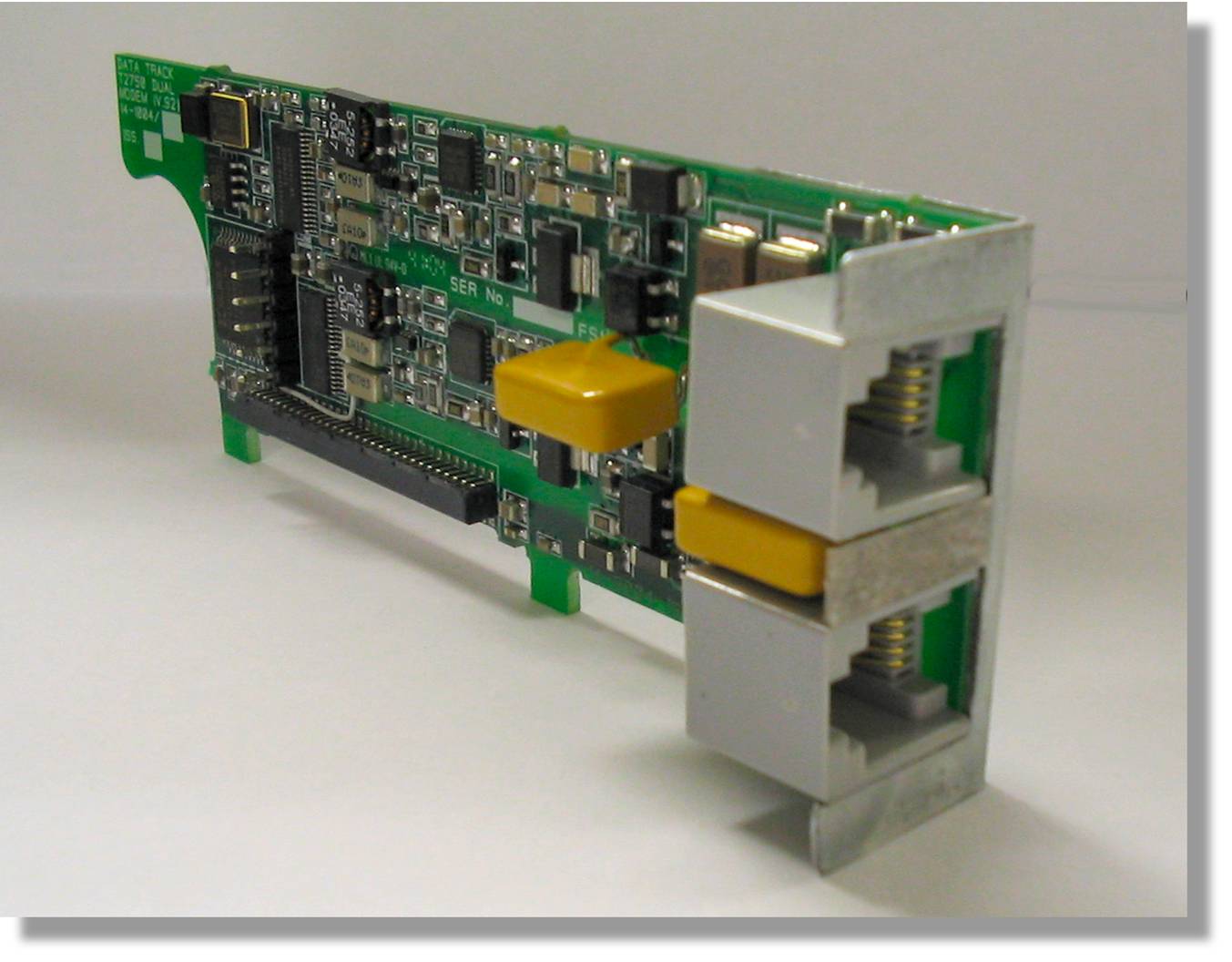
Single and dual V.92 PSTN modem card
|
|
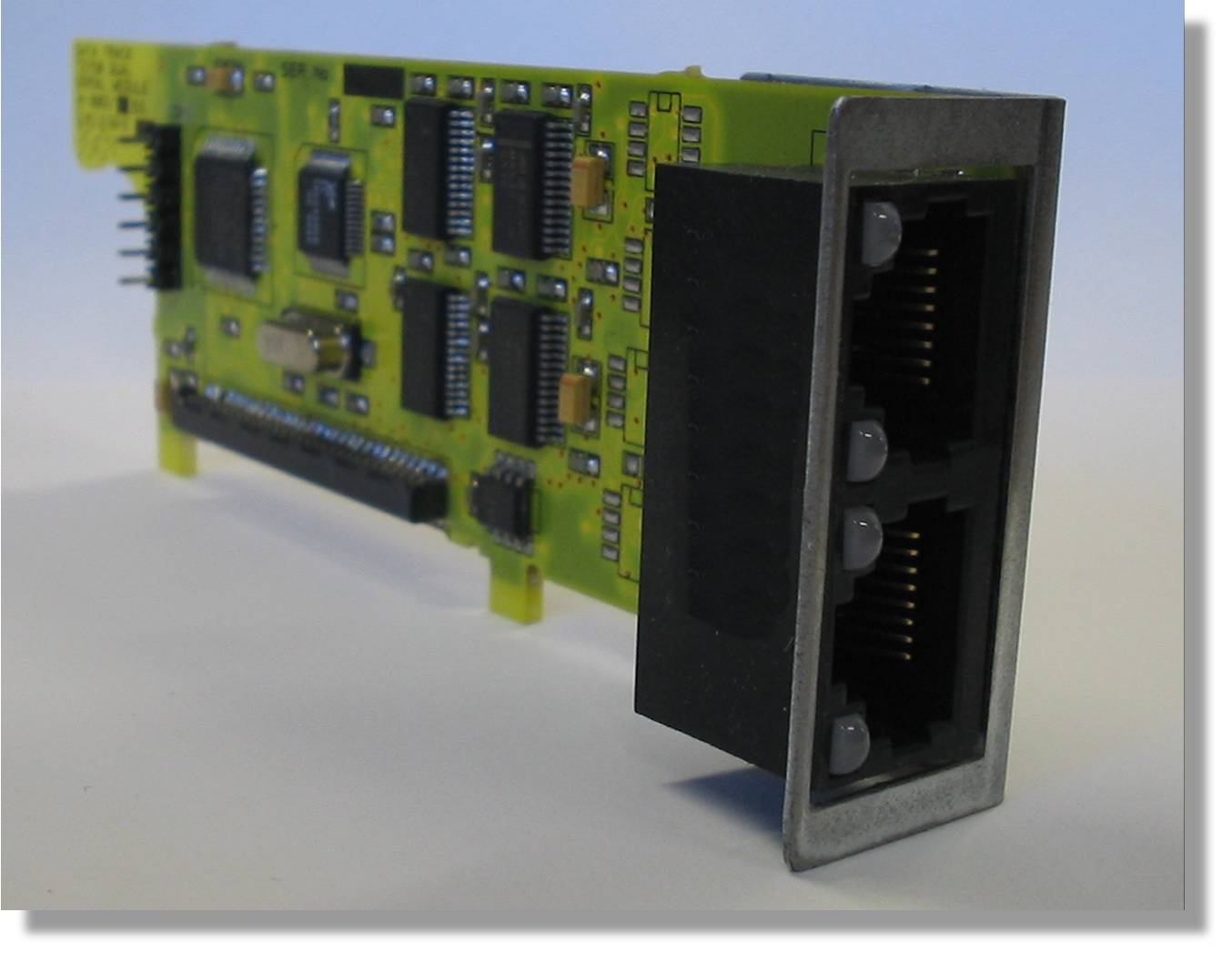
Single and dual RS-232 serial card with RJ-45 interface
|
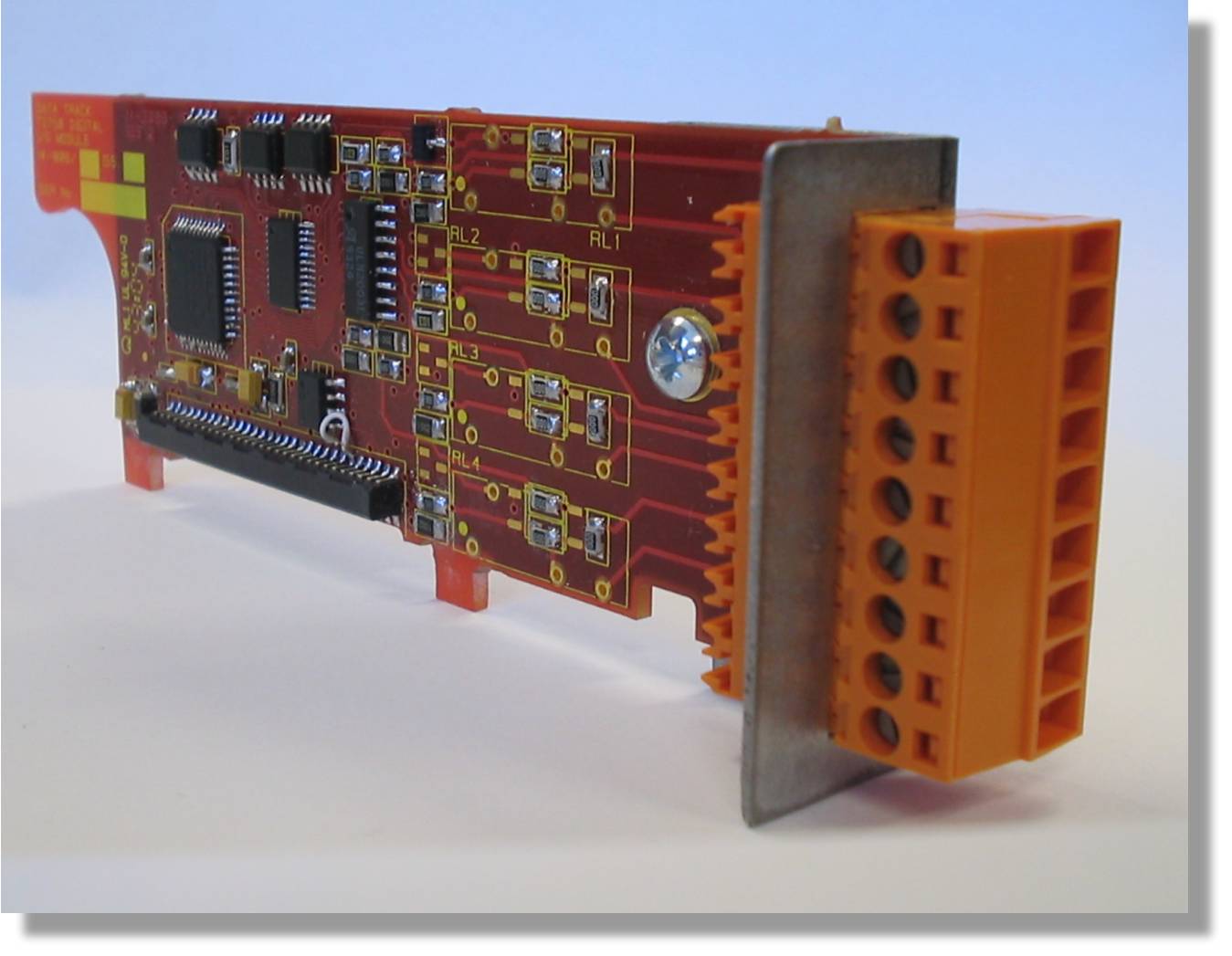
Contact closure card for 8 devices with detachable terminal block |

Features:
-
Secure Remote Access - provides connectivity to voice and data communication
devices across local area, wide area, Internet and dial-up networks using proven
Authorization, Authentication, and Auditing mechanisms. This provides a solid
and secure foundation for keeping critical voice and data network infrastructure
functioning reliably.
-
No Central Server - the Tracker 2750 has
sufficient memory to store its own access lists, thus eliminating the need
to check for authorization from a central server. This can be
important if connectivity to your central networking management center has
been severed. Synchronization of Tracker access lists can be done through
your own programs.
-
Device Alarm Monitoring - is a maintenance tool that can provide an operational
overview of system or equipment performance, 24 hours a day, and informs you of
any alarm conditions that may occur. This ensures maximum equipment
availability, minimum system downtime and consequently, improved customer
service levels. Output can be sent simultaneous to any number of standard
network monitoring tools. You can even have the Tracker 2750 store the
alarms and only send them once some pre-determined threshold has been
reached.
-
Open Operating System - the Tracker 2750 is based
upon the Linux operating system instead of proprietary systems like other
devices.
-
Available SDK - because of its large addressable
flash memory, you can develop and run your own custom applications directly
from the Tracker 2750. Many conditions can be monitored and immediate
action taken without having to wait for the condition to be observed by your
central networking management center. The Tracker 2750 makes use of
Python scripting, an easy-to-learn and use industry standard language.
-
Two Factor Authentication - When a stronger access
method is needed to further protect dial-up access on the Tracker 2750,
there are two different challenge response mechanisms available within the
system. The first is a token-based, two-factor authentication
mechanism. The second is a hardware-based, two-factor authentication
mechanism. In this configuration, a Tracker 2720, which acts as a secure
modem, is attached to a serial port of a system administrator or support
engineer’s PC. The user runs a terminal program on the PC to access the
Tracker 2720 as an outbound modem. A phone number is selected within the
terminal program and a dial-up connection is established with a Tracker 2700
at the remote node where maintenance services are to be performed. The
Tracker systems attempt to authenticate with each other based on a
standards-based, two-factor authentication mechanism.
-
Remote Backup and Remote Restore - because of its
extended memory capacity, the Tracker 2750 can easily store configurations
of local devices (routers, switches, etc.) so that they can be quickly
restored and even re-booted remotely.
-
VPN - support for VPN tunnels for secure
connections across TCP/IP local and wide area networks comes standard with
the Tracker 2750.


Benefits:
- Cost reductions from a decrease in technician dispatches to remote locations through:
- Local storage/access enabling remote restoration of device configurations.
- Ability to power cycle remote devices.
- Superior service levels resulting in improved Customer Satisfaction through
:
- Quicker response to problems.
- Shortening or circumventing of outages.
- Improved management of system administration activity by adding the following to your environment:
- Consistent, secure access for remote and local network devices.
- Session auditing of administration activity.
- Benefit of improved network infrastructure protection from compromise or failure.
- Future-proofs the environment because platform is extensible and programmable.
|
